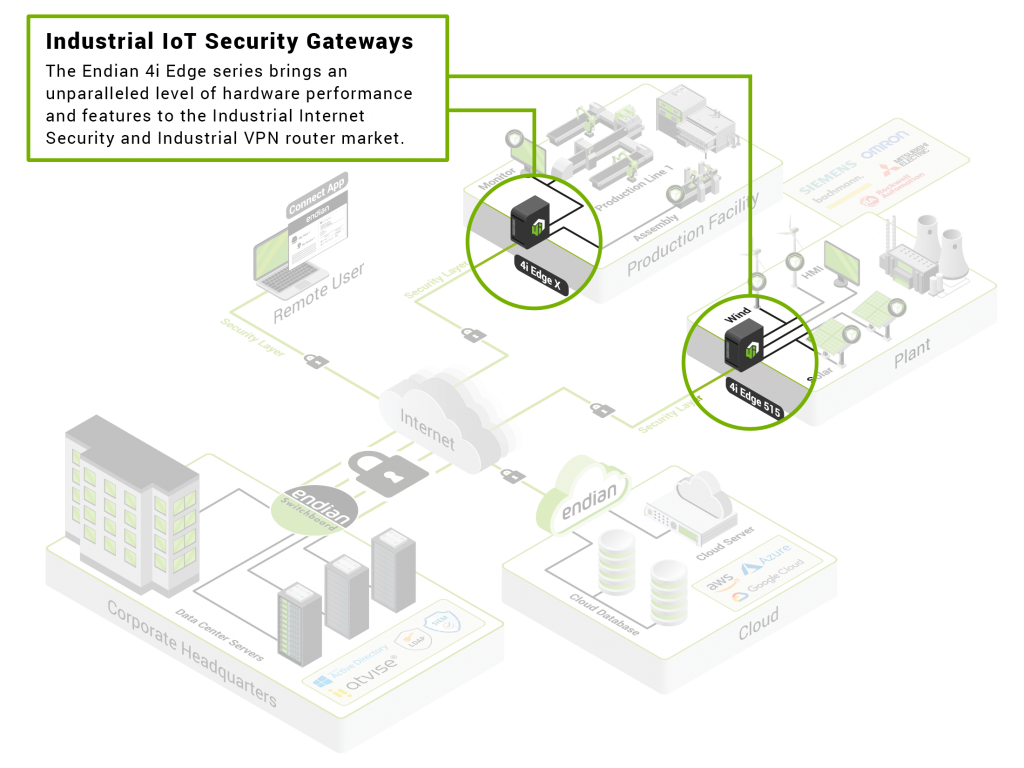
Experience advanced OT cybersecurity with the Endian 4i Edge Series. These industrial IoT gateways offer robust hardware, ensuring reliable performance and secure connectivity. With built-in Docker container support for Edge Computing, organizations can deploy and manage applications with ease.
Endian 4i
Experience advanced OT cybersecurity with the Endian 4i Edge Series. These industrial IoT gateways offer robust hardware, ensuring reliable performance and secure connectivity. With built-in Docker container support for Edge Computing, organizations can deploy and manage applications with ease.
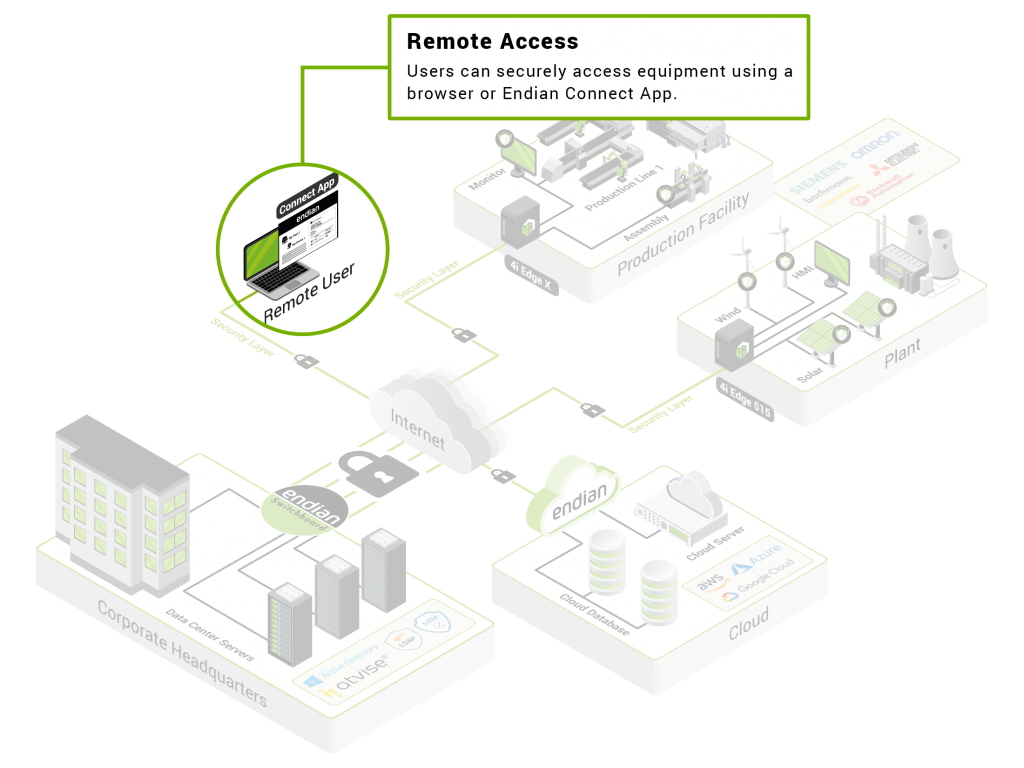
Secure Remote Maintenance

Zero Trust Architecture
With the arrival of the digital transformation in combination with a distributed and global remote workforce, organizations can no longer use legacy security models. In the new Zero Trust architecture, businesses trust less and verify everything so they can reduce their attack surface using fine-grained access, authorization and security policies. In addition, a Zero Trust environment ensures stronger and better compliance and audit efforts.

Microsegmentation
As part of the Zero Trust architecture, creating smaller and more targeted network zones increases security while reducing risk exposure. By utilizing powerful security policies to enforce zone boundaries organizations can ensure only approved network communications. As required, businesses can create least-privilege secure pathways using technologies like NAT (Network Address Translation) or VPN (Virtual Private Network).
Threat Management
For approved network communications, a business must go deeper to ensure they are actually safe and secure. The threat management toolset helps to detect and stop advanced threats and malware from infiltrating business networks. Using deep-packet intrusion detection and prevention to identify and enforce security policies. In addition, application layer and protocol analysis helps to ensure traffic validity and block traffic regardless of IP address or port.
Edge Computing
The concept of edge computing simply means utilizing computing resources at the edge of the network (instead of the central network or datacenter). By leveraging Docker and container technology, organizations can leverage micro services and applications to replace or extend edge network capabilities. Whether it's data collection, analytics, monitoring or automation the possibilities are endless for edge computing.
Network Visibility and Monitoring
Before an organization can implement a Zero Trust model, they must identify and assess every single device on their network. Using traditional methods can be costly and resource intensive and requires frequent and constant monitoring. With Network Awareness, a business can quickly and easily achieve and maintain visibility to discover all connected assets and protect themselves from threats.
Ruggedized Hardware
Industrial locations can vary greatly and are more exposed to environmental and safety risks. Due to this, the hardware must meet certain criteria including form factor and operating conditions. In addition, there are unique power, connectivity and communication constraints that must be taken into account. This is why Endian 4i hardware is purpose built to meet the needs of industrial networks and environments.

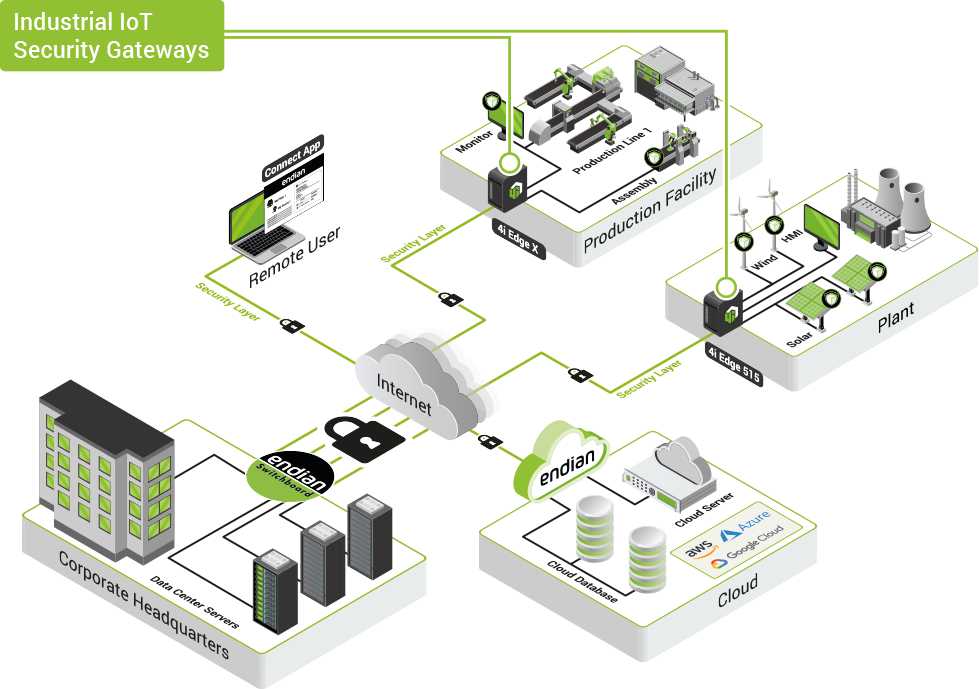
Anatomy of a Secure Digital Platform
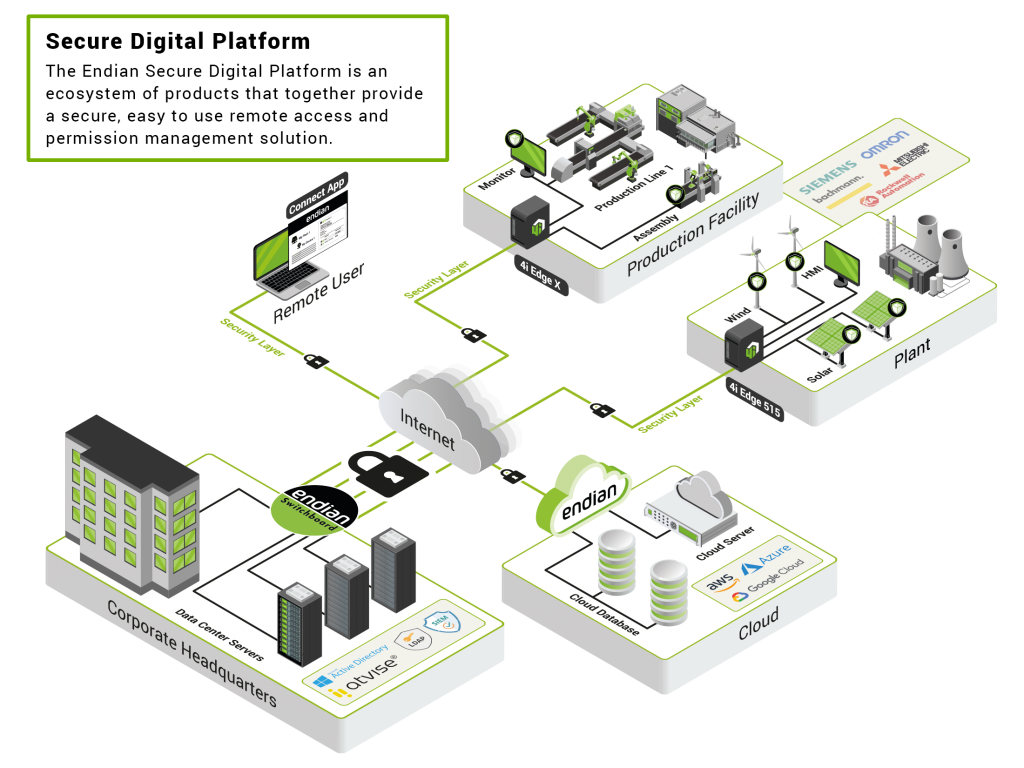
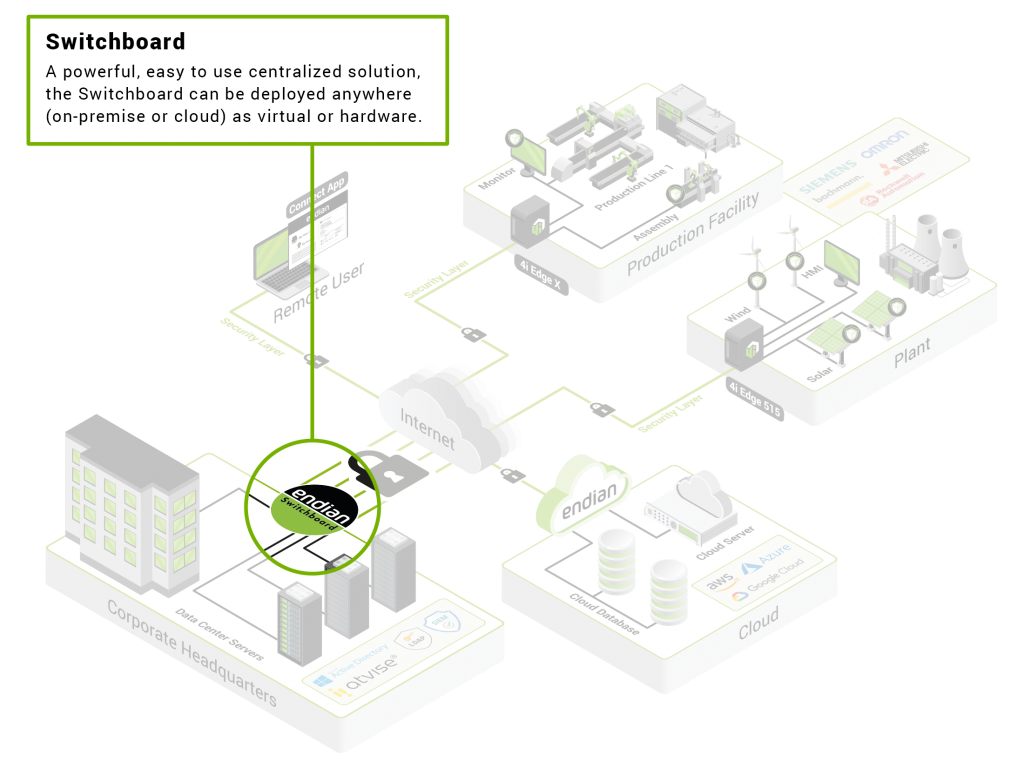
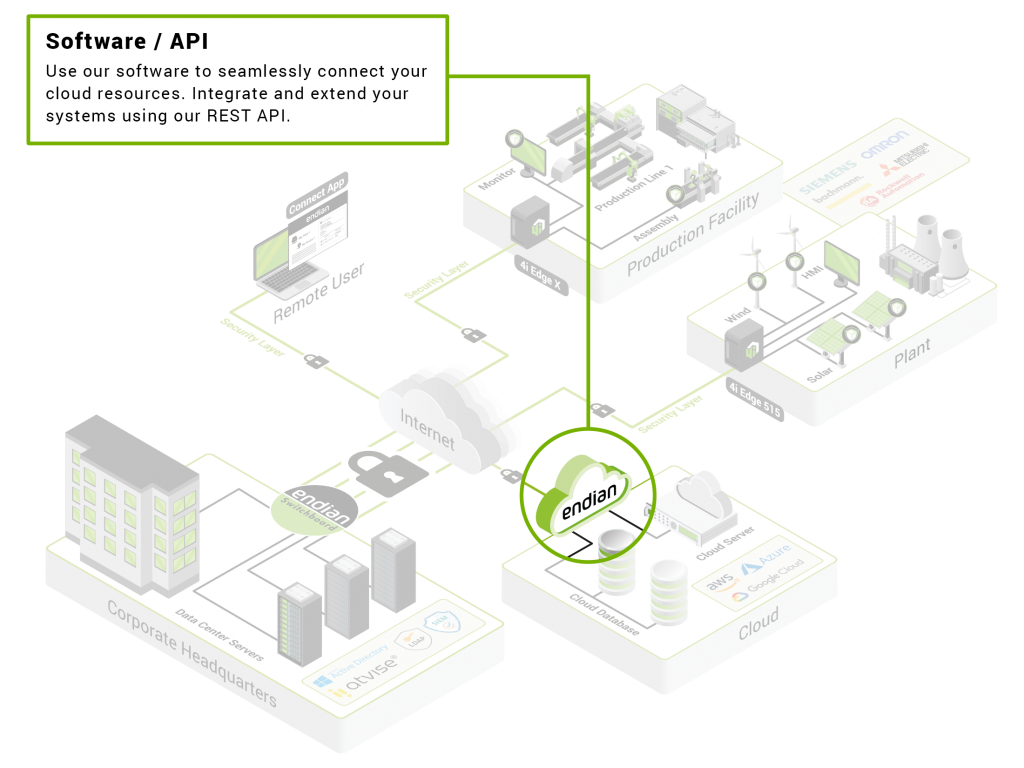
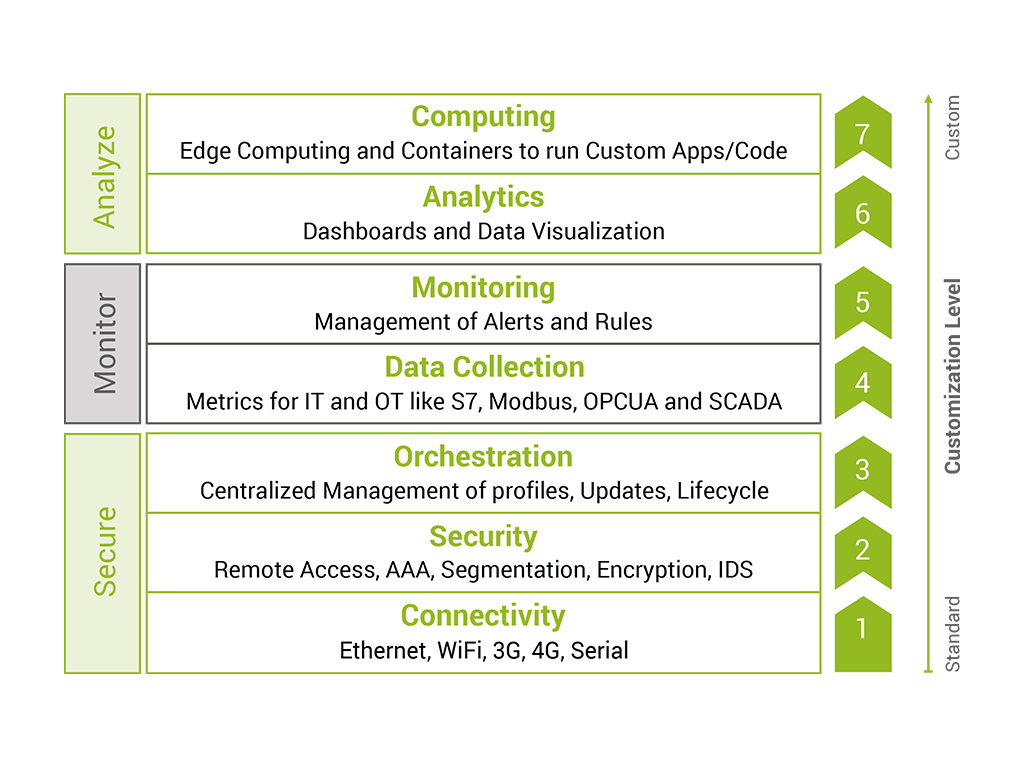
EndianOS: Engine for a Secure Digital Transformation
Unlock the potential of your digital journey with EndianOS, the robust operating system designed to meet the challenges of IT and OT convergence in the digital age.


Endian 4i Hardware
Purpose-built and ruggedized industrial hardware with advanced cybersecurity, connectivity and edge computing capabilities.

Endian 4i Software
Turn any IoT Gateway/PC (x86) into an advanced industrial cybersecurity appliance to protect and connect networks, machines and data.
