Small and Medium sized Businesses (SMBs), educational institutions, and government organizations form the backbone of our digital infrastructure. As they rapidly transition to more sophisticated networks, the protection of devices, data, and overall digital ecosystems becomes paramount. Navigating this digital era requires a blend of operational integrity, trust-building, and regulatory compliance.
IT Cybersecurity: Secure devices and computers in business & organizational networks
Premier IT Cybersecurity solutions by Endian for business & organizational networks. Ensure robust protection for devices, computers, and digital infrastructure.
Secure Devices and Computers in Business and Organizational and Networks

Unified Threat Management
For SMBs, educational institutions, and government agencies alike, a holistic approach to cybersecurity is non-negotiable. Counteract everything from malware intrusions to sophisticated phishing campaigns, ensuring that real-time threats are both detected and mitigated.

Content Filtering
Safeguard users from harmful or inappropriate content. Implement web filters that block access to risky sites and content categories, ensuring safe browsing and aligning with institutional or organizational policies. At the same time you can also ensure high productivity of your staff allowing only access to appropriate content.

Centralized Device Monitoring & Management
Streamline your IT operations with central device management. Monitor, manage, and configure devices within the network for a more cohesive and integrated security approach.

Advanced Intrusion Detection and Prevention
Protecting your network's perimeter isn't enough. Proactively detect potential internal threats and neutralize them before they escalate into larger issues.

Encrypted & Secure Connectivity
Ensure that data transfers, be it a business transaction, academic content, or government communication, are always encrypted. This prevents unauthorized access, ensuring data integrity and confidentiality.

Manage BYOD and Guest Access
Facilitate controlled and secure internet access for employees, guests, visitors, or temporary users. Whether it's students in a university, clients in an SMB environment, or visitors in a government building, provide them with a dedicated and secure web access point, ensuring the internal network remains uncompromised.

Secure Remote Access
Grant users secure and efficient remote access to essential resources. This is vital for remote workers in SMBs, students accessing academic resources, or government officials connecting from different locations.

Conclusion:
In the modern digital landscape, SMBs, educational institutions, and government organizations need tailored cybersecurity solutions. With Endian's suite of offerings, these entities can traverse the digital realm with unmatched confidence, ensuring robust protection for their devices and networks.
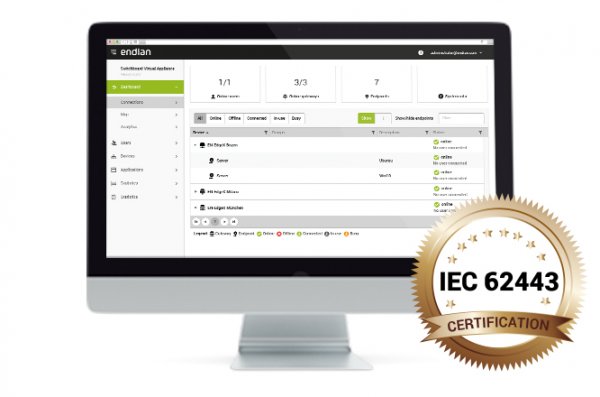
Endian Switchboard
The Endian Switchboard is the heart of the Endian Secure Digital Platform that provides secure remote access to field equipment.

Endian 4i (OT Environments)
The Endian 4i Edge series brings an unparalleled level of hardware performance and features to the Industrial Internet Security and Industrial VPN router market.
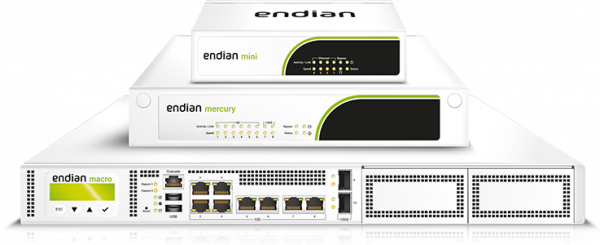
Endian UTM (IT Environments)
A complete range of specifically designed appliances integrating our UTM software for the security needs of everyone, from branch offices and industrial facilities to large networks.
